Cyber Strategy
What is a Cyber Strategy?
Cyber is an abbreviation of cybernetics, the science of control and communication, as described by Norbert Wiener more than 70 years ago. The field of cybernetics analyses systems and their feedback loops. Cybernetic is derived from the Greek word kybernetes, which means steersman or sea captain.
The usage of cyber as a prefix for computer related terms first evolved in the 1980s and has gained popularity ever since. There is no clear explanation for our fascination about and enthusiastic usage of the word cyber. As such, the prefix cyber is meaningless. One may use Ross Ashby’s description of the term stability in cybernetics, where he describes that “Today’s terminology is unsatisfactory and confused; I shall not attempt to establish a better”.[1] The idea of continuous, never resting bits of data racing around the world in an ever-growing network were perfectly suited for the futuristic sounding idea of a “cyber-space”.
Components of a Cyber Strategy
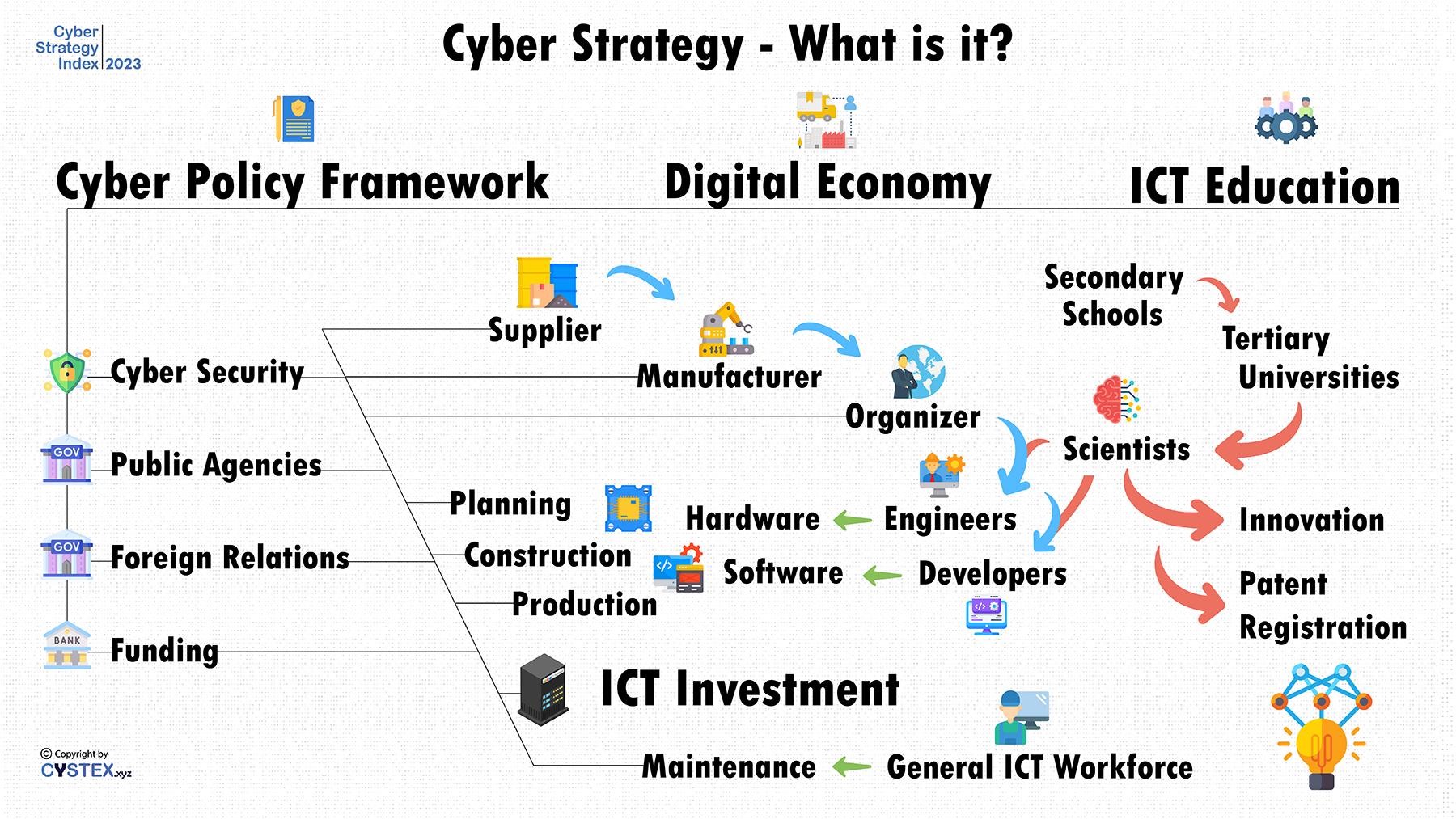
Cyber Policy Framework
- Cyber Security
- Public Agencies
- Foreign Relations
- Funding
Digital Economy
- Supplier
- Manufacturer
- Organizer
- ICT Investment
ICT Education
- Secondary Schools
- Tertiary Universities
- Scientists
- Engineers
- Developers
- Innovation
- Patent Registration
Importance of Each Component
Cyber Policy Framework
- Guidelines, regulations, and governance structures
- Ensures a secure digital environment
- Includes cyber security measures
- Defines roles of public agencies
- Promotes international cooperation
- Allocates funding for secure digital infrastructure
Digital Economy
- Growth and innovation
- Relies on a complex ecosystem of suppliers, manufacturers, organizers, and investors
- Suppliers provide raw materials
- Manufacturers create digital products
- Organizers coordinate stakeholders
- ICT investments support technology development
ICT Education
- Foundation for the future digital economy and cyber strategy
- Secondary schools provide basic digital skills
- Tertiary universities offer advanced education and research
- Professionals such as scientists, engineers, and developers innovate and create new technologies
- Protecting intellectual property through patent registration encourages ongoing investment and development
China's Digital Strategy
“Imagine how it could change China” is a statement about the future role of the internet and the cyberspace within China from Bill Clinton in his speech on March 9, 2000 on the China Trade Bill and China’s inclusion into the World Trade Organization (WTO).[2] Clinton was the first US President who saw and witnessed the impact of the internet on the US society, its industries, cultures and institutions (cf. Guo 2021, p. 24 ff.). He similarly imagined a fundamental disturbance of old technology in all parts of everyday life in China. 15 years later, Xi Jinping speaks at the opening ceremony of the second World Internet Conference in Wuzhen about the deep integration of the internet into China’s economic and social development and the life of the Chinese people.[3] China’s internet user base rose from around 25 million in 2000 to over 670 million in 2015 or from 2% to over 50% of the population.[4] The meteoric rise from a technological development country to the biggest internet community on the planet was by no means a lucky coincidence. With Tencent founded in November of 1998 and Alibaba in April of 1999, the two most prominent IT players in the Chinese market played an important role from very early on.
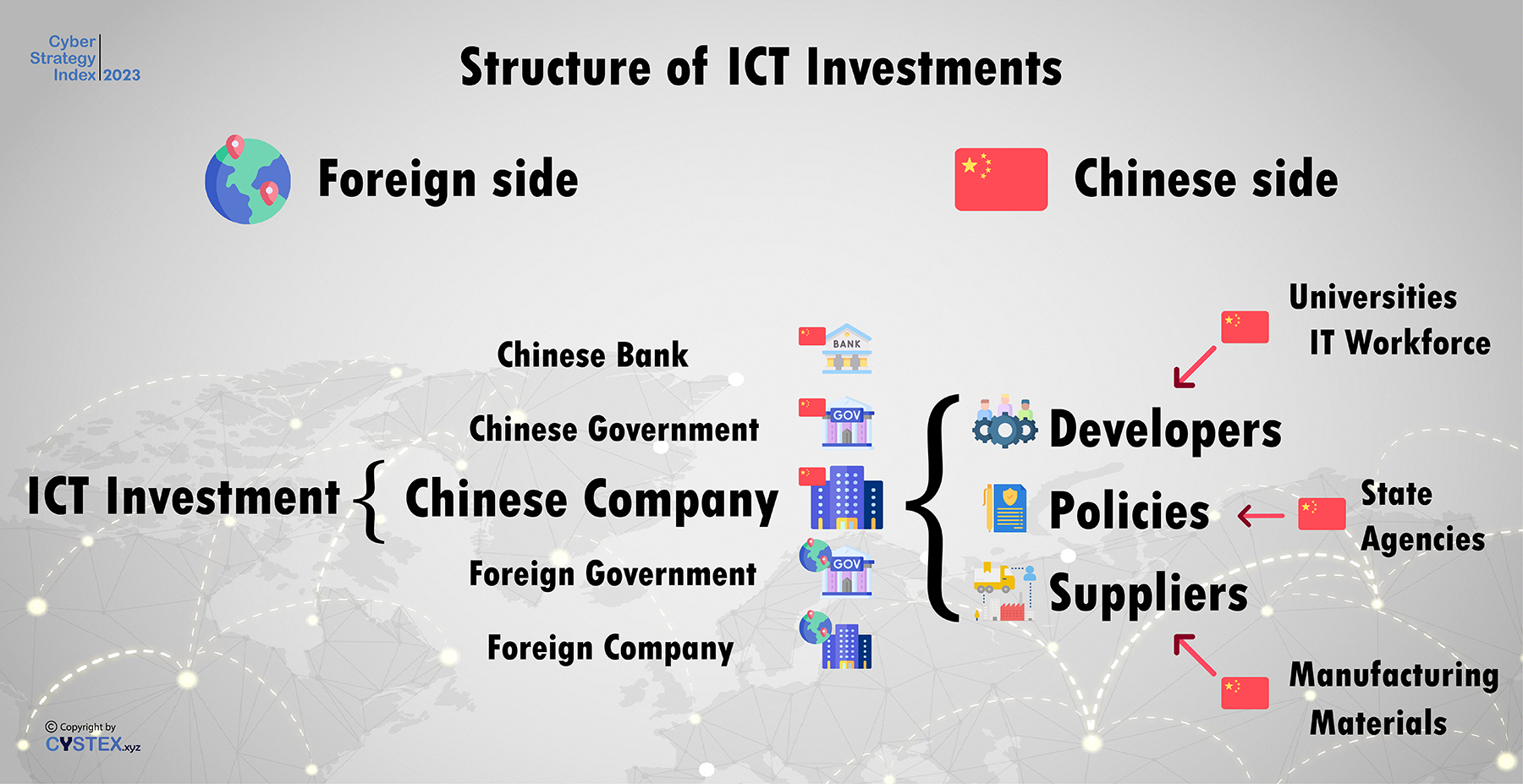
Structure of ICT Investments
ICT investments involve a complex interplay between the foreign side and the Chinese side. On the foreign side, key players include the Chinese bank providing financing, the Chinese government, Chinese companies, and the foreign government and companies collaborating on the investment.
On the Chinese side, critical components are the universities training the IT workforce, developers creating software and solutions, suppliers providing necessary manufacturing materials, and state agencies overseeing policies. This multi-faceted structure enables China to comprehensively develop and implement its cyber strategy both domestically and abroad.
CYSTEX: Systematic Analysis of Cyber Strategies
While the Belt and Road Initiative and Digital Silk Road are two tremendously important policies regarding size and scope, they only offer part of the equation for deciphering China’s global digital ambitions. Certain elements prohibit existing research around the topic from encircling the necessary data and scale needed for a systematic approach. The existing research conducted to identify the determining constituents of China’s global digital strategy lacks a systematic approach.
CYSTEX tries to lower this research gap and offers an analysis framework for the systematic analysis of cyber strategies. ICT investments are main driver for digital development and offer tremendous insights into their correlation to digital development and domestic cyber policy frameworks of selected countries. By examining the complex web of actors and components involved, CYSTEX aims to provide a comprehensive understanding of China's cyber strategy and its global implications.
Sources
[1] Roger Conant describes in the book Mechanisms of Intelligence: Ashby’s Writings on Cybernetics the origins of cybernetics and Ashby’s conceptualization of it: http://www.rossashby.info/Ashby-Mechanisms_of_intelligence.pdf
[2] Full transcript of Bill Clinton’s speech on March 9, 2000 on the China Trade Bill: https://www.iatp.org/sites/default/files/Full_Text_of_Clintons_Speech_on_China_Trade_Bi.htm
[3] Full transcript of Xi Jinping’s speech at the opening ceremony of the Second World Internet Conference on December 16, 2015: https://www.fmprc.gov.cn/eng/wjdt_665385/zyjh_665391/201512/t20151224_678467.html
[4] The World Bank: Individual Internet Users % of Population – China 1990 - 2020: https://data.worldbank.org/indicator/IT.NET.USER.ZS?locations=CN